Data Protection Ensure Business Security
Meet Compliance Requirements
Follow Global Regulations
Privacy data protection
Sensitive Content Control
Reduce Data-leakage Risk
Cross-organization Secure Sharing
Data Encryption Strategy
Watermark
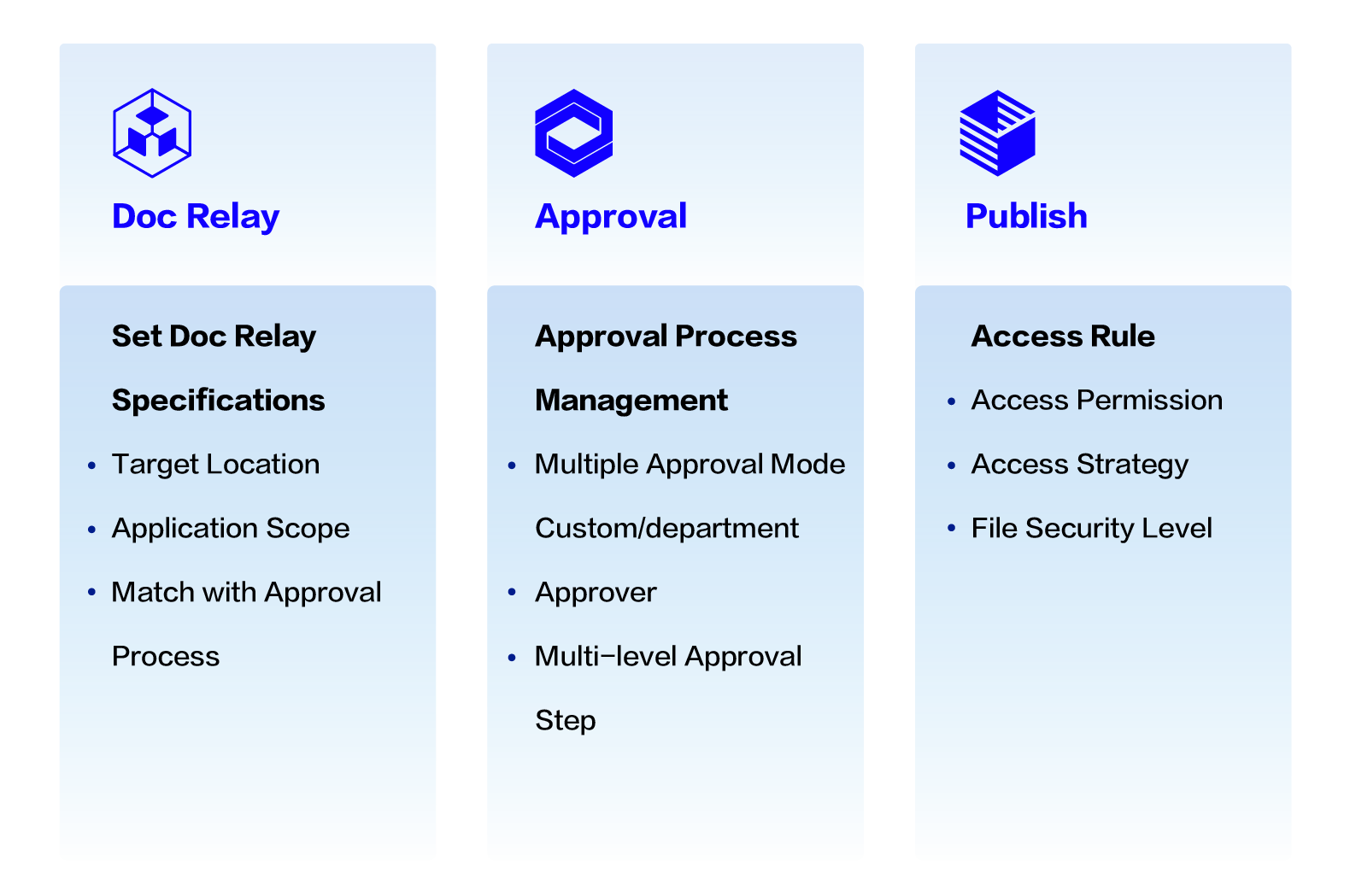
Enhance Data Manage-ment Standardization
Organizational approval Process
Access Control
Security Level Control
Reduce Data-Loss Risk
Anti-ransomware
Secondary Recycle Bin
File Backup
Data Protection Ensure Business Security
Meet Compliance Requirements
Follow Global Regulations
Privacy data protection
Sensitive Content Control
Reduce Data-leakage Risk
Cross-organization Secure Sharing
Data Encryption Strategy
Watermark
Enhance Data Management Standardization
Organizational approval Process
Access Control
Security Level Control
Reduce Data-Loss Risk
Anti-ransomware
Secondary Recycle Bin
File Backup
End-to-End Security Features
End-to-End Security Features
-
Prevention Stage
-
Protection Stage
-
Traceability Stage
Explore More Scenarios of Data Security Application
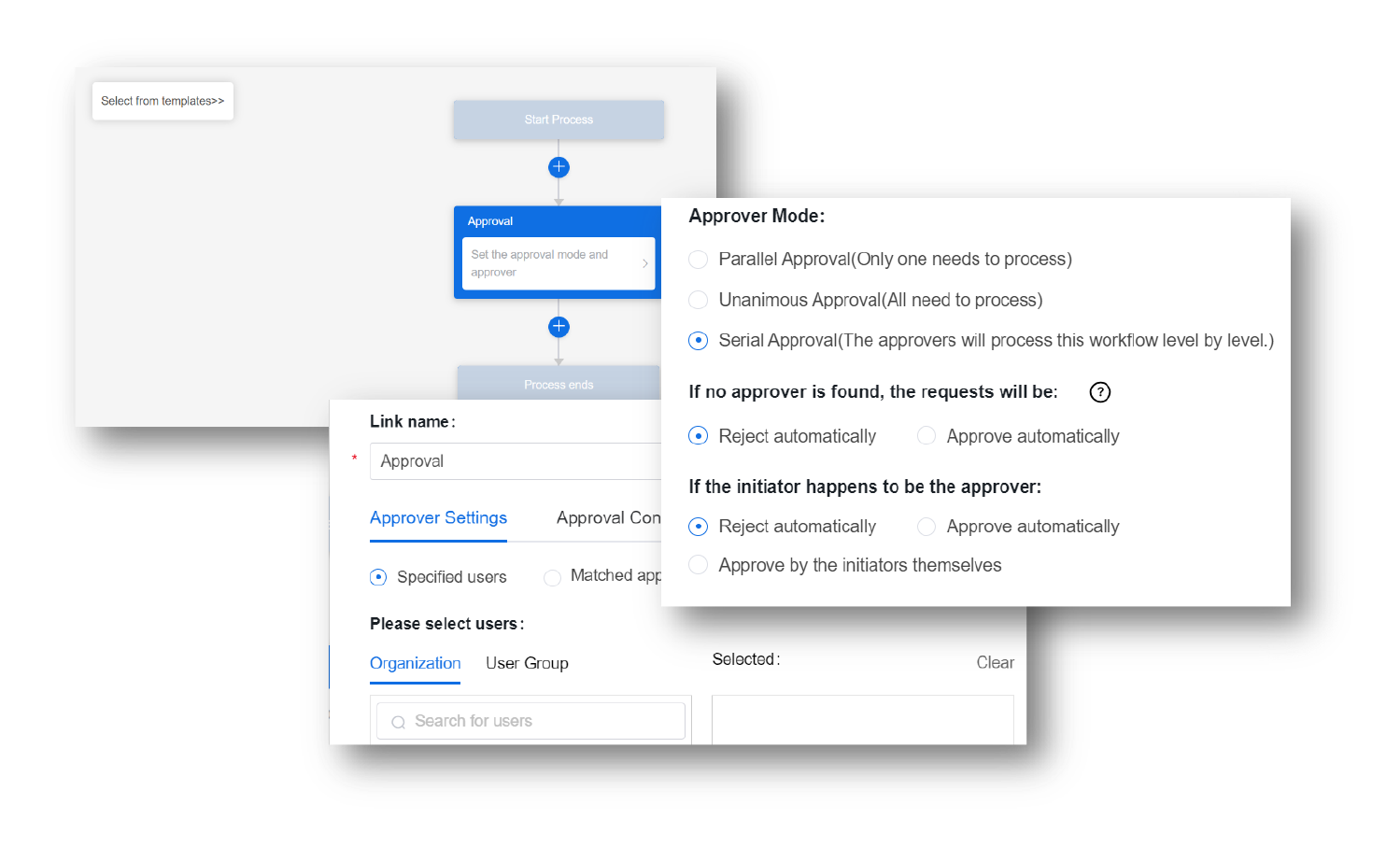
Release of Regulations
- Automate document release and review processes to reduce time waste and free up human resources
- A variety of security policies control to prevent data loss and leakage, and to ensure content security
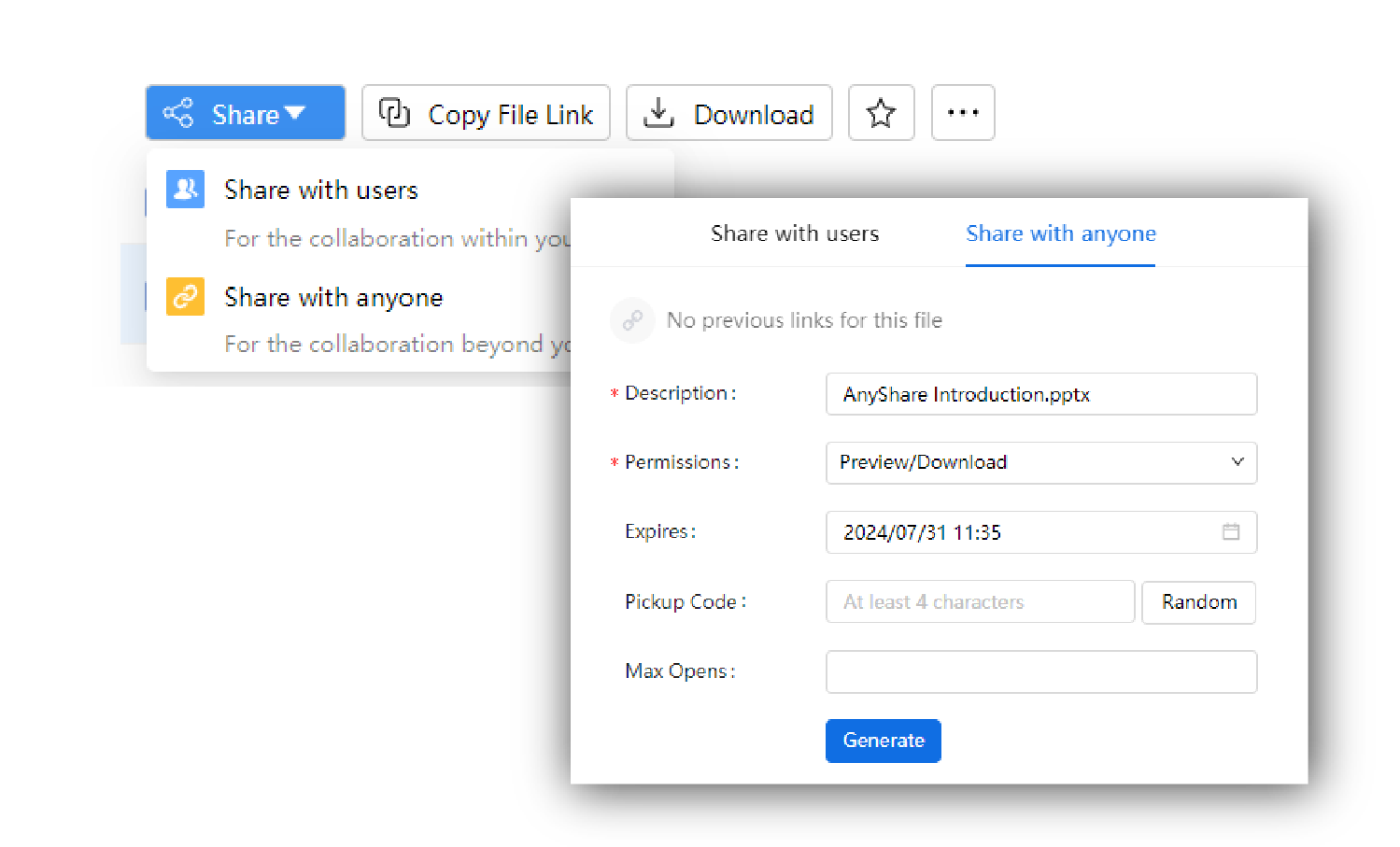
Cross-organizational Data Sharing
- External data sharing fully controlled by permissions and policies ensuring secure flow of files across organizations
- Multi-dimensional data reports visually demonstrate shared access to reduce data risk and maintain operational compliance
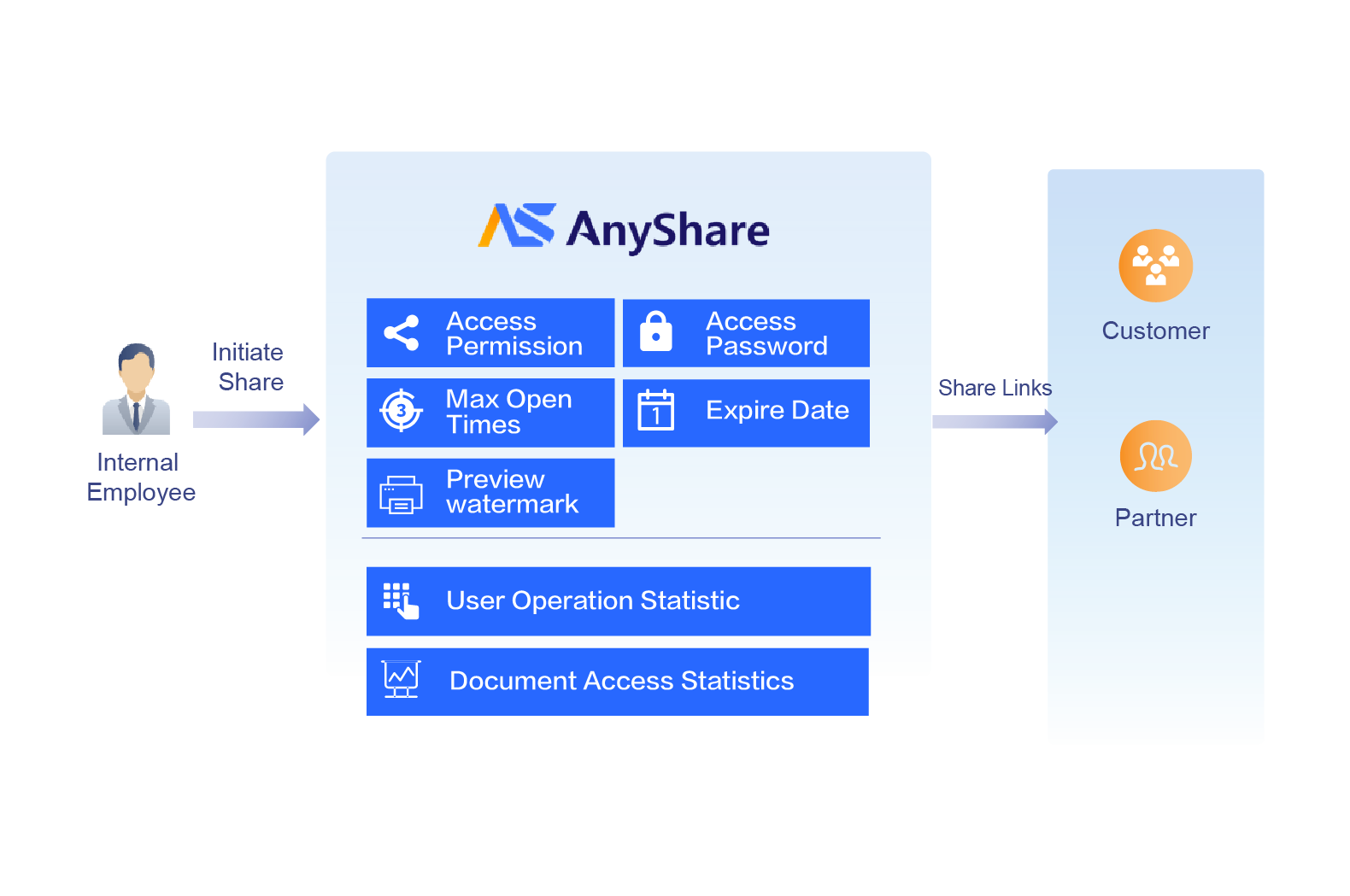
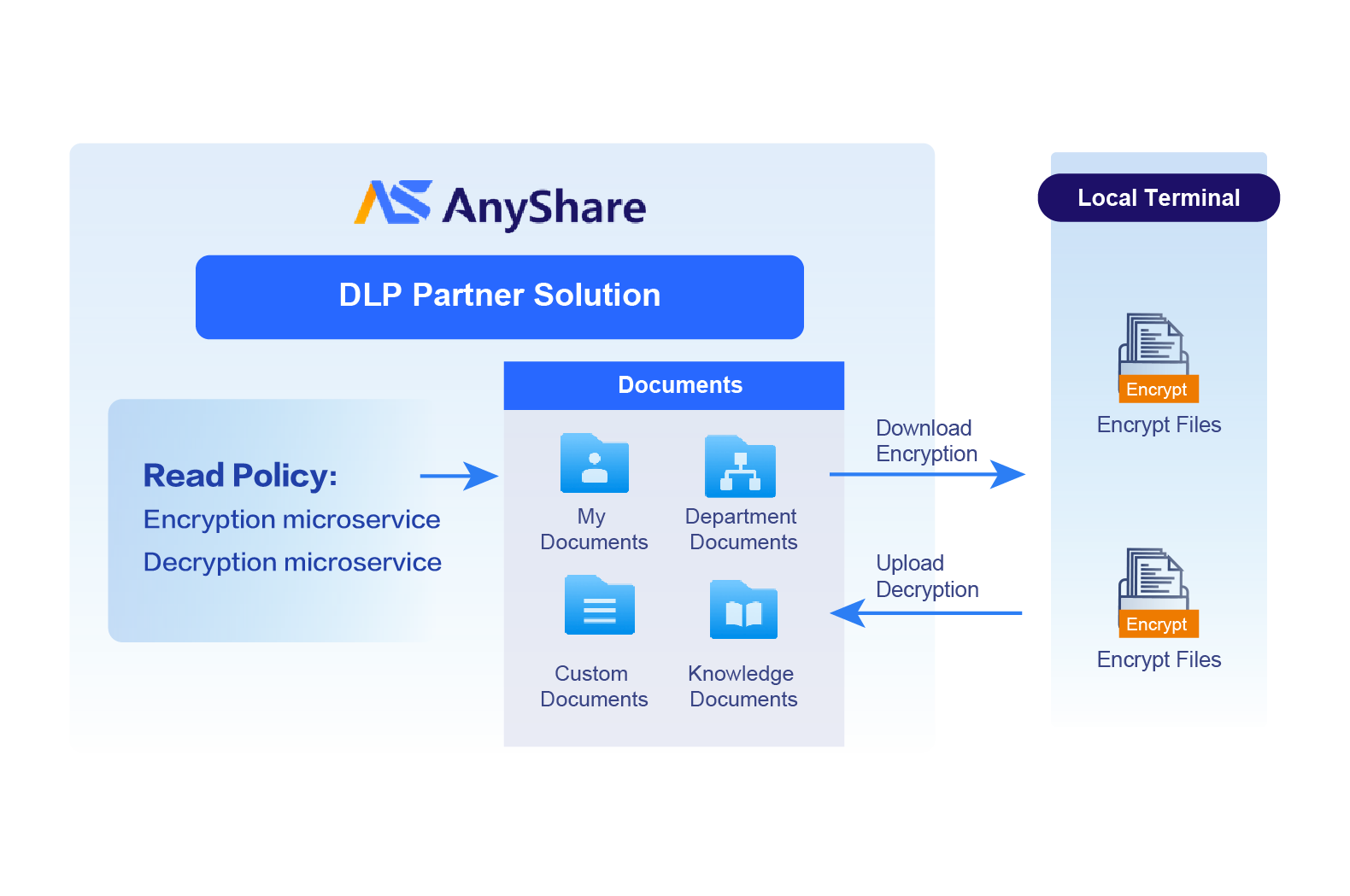
Data Leak Protection
- After the encrypted file is uploaded to AnyShare, it can be decrypted and use online
- Controlled files are automatically encrypted when downloaded from AnyShare, ensuring the secure use of data in business processes
Explore More Scenarios of Data Security Application

Release of Regulations
- Automate document release and review processes to reduce time waste and free up human resources
- A variety of security policies control to prevent data loss and leakage, and to ensure content security

Cross-organizational Data Sharing
- External data sharing fully controlled by permissions and policies ensuring secure flow of files across organizations
- Multi-dimensional data reports visually demonstrate shared access to reduce data risk and maintain operational compliance

Data Leak Protection
- After the encrypted file is uploaded to AnyShare, it can be decrypted and use online
- Controlled files are automatically encrypted when downloaded from AnyShare, ensuring the secure use of data in business processes